@J0E
I did a quick little image update Dockerfile for you, that you can use in Portainer to create an updated image. This particular example takes the current channels-dvr:tve image and updates the base OS packages. This should work on whatever CDVR image you need.
This is a fast and easy process, and unlike the CDVR developers that have to consider ramifications for a much wider audience, this image has an audience of one -- you. 
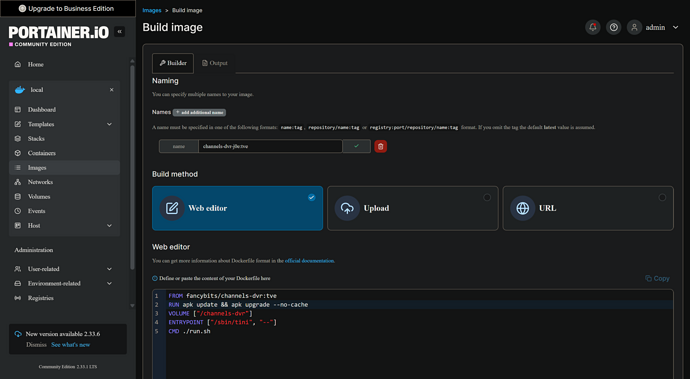
Dockerfile:
FROM fancybits/channels-dvr:tve
RUN apk update && apk upgrade --no-cache
VOLUME ["/channels-dvr"]
ENTRYPOINT ["/sbin/tini", "--"]
CMD ./run.sh
It'll look like this in Portainer-Images:
The output from the build (which is very fast), will look like this:
Step 1/5 : FROM fancybits/channels-dvr:tve
---> cd4385b47a5b
Step 2/5 : RUN apk update && apk upgrade --no-cache
---> Running in 6f856e5732a8
fetch https://dl-cdn.alpinelinux.org/alpine/v3.21/main/x86_64/APKINDEX.tar.gz
fetch https://dl-cdn.alpinelinux.org/alpine/v3.21/community/x86_64/APKINDEX.tar.gz
v3.21.5-137-g5140a0d78c3 [https://dl-cdn.alpinelinux.org/alpine/v3.21/main]
v3.21.5-134-g41635b0fc8a [https://dl-cdn.alpinelinux.org/alpine/v3.21/community]
OK: 25443 distinct packages available
fetch https://dl-cdn.alpinelinux.org/alpine/v3.21/main/x86_64/APKINDEX.tar.gz
fetch https://dl-cdn.alpinelinux.org/alpine/v3.21/community/x86_64/APKINDEX.tar.gz
Upgrading critical system libraries and apk-tools:
(1/1) Upgrading apk-tools (2.14.6-r2 -> 2.14.6-r3)
Executing busybox-1.37.0-r9.trigger
Continuing the upgrade transaction with new apk-tools:
fetch https://dl-cdn.alpinelinux.org/alpine/v3.21/main/x86_64/APKINDEX.tar.gz
fetch https://dl-cdn.alpinelinux.org/alpine/v3.21/community/x86_64/APKINDEX.tar.gz
(1/45) Upgrading musl (1.2.5-r8 -> 1.2.5-r9)
(2/45) Upgrading busybox (1.37.0-r9 -> 1.37.0-r14)
Executing busybox-1.37.0-r14.post-upgrade
(3/45) Upgrading busybox-binsh (1.37.0-r9 -> 1.37.0-r14)
(4/45) Upgrading alpine-release (3.21.2-r0 -> 3.21.5-r0)
(5/45) Upgrading ca-certificates-bundle (20241121-r1 -> 20250911-r0)
(6/45) Upgrading libcrypto3 (3.3.2-r4 -> 3.3.5-r0)
(7/45) Upgrading libssl3 (3.3.2-r4 -> 3.3.5-r0)
(8/45) Upgrading ssl_client (1.37.0-r9 -> 1.37.0-r14)
(9/45) Upgrading libexpat (2.6.4-r0 -> 2.7.3-r0)
(10/45) Upgrading libpng (1.6.44-r0 -> 1.6.53-r0)
(11/45) Upgrading libffi (3.4.6-r0 -> 3.4.7-r0)
(12/45) Upgrading libblkid (2.40.4-r0 -> 2.40.4-r1)
(13/45) Upgrading libmount (2.40.4-r0 -> 2.40.4-r1)
(14/45) Upgrading glib (2.82.4-r0 -> 2.82.5-r0)
(15/45) Upgrading xz-libs (5.6.3-r0 -> 5.6.3-r1)
(16/45) Upgrading libxml2 (2.13.4-r3 -> 2.13.9-r0)
(17/45) Upgrading tiff (4.7.0-r0 -> 4.7.1-r0)
(18/45) Upgrading gtk-update-icon-cache (3.24.43-r2 -> 3.24.49-r0)
(19/45) Upgrading cairo (1.18.2-r1 -> 1.18.4-r0)
(20/45) Upgrading cairo-gobject (1.18.2-r1 -> 1.18.4-r0)
(21/45) Upgrading libtasn1 (4.19.0-r2 -> 4.20.0-r0)
(22/45) Upgrading gtk+3.0 (3.24.43-r2 -> 3.24.49-r0)
(23/45) Upgrading icu-data-full (74.2-r0 -> 74.2-r1)
(24/45) Upgrading llvm19-libs (19.1.4-r0 -> 19.1.4-r1)
(25/45) Upgrading hwdata-pci (0.390-r0 -> 0.393-r0)
(26/45) Upgrading libuuid (2.40.4-r0 -> 2.40.4-r1)
(27/45) Upgrading giflib (5.2.2-r0 -> 5.2.2-r1)
(28/45) Upgrading libjxl (0.10.3-r0 -> 0.10.4-r0)
(29/45) Upgrading cjson (1.7.18-r0 -> 1.7.19-r0)
(30/45) Upgrading mbedtls (3.6.2-r0 -> 3.6.5-r0)
(31/45) Upgrading libsodium (1.0.20-r0 -> 1.0.20-r1)
(32/45) Upgrading icu-libs (74.2-r0 -> 74.2-r1)
(33/45) Upgrading sqlite-libs (3.47.1-r0 -> 3.48.0-r4)
(34/45) Upgrading nss (3.107-r0 -> 3.109-r0)
(35/45) Upgrading openh264 (2.5.0-r0 -> 2.6.0-r0)
(36/45) Upgrading libxslt (1.1.42-r1 -> 1.1.42-r2)
(37/45) Upgrading chromium (132.0.6834.83-r0 -> 136.0.7103.113-r0)
(38/45) Upgrading c-ares (1.34.3-r0 -> 1.34.6-r0)
(39/45) Upgrading libcurl (8.11.1-r0 -> 8.14.1-r2)
(40/45) Upgrading curl (8.11.1-r0 -> 8.14.1-r2)
(41/45) Upgrading musl-utils (1.2.5-r8 -> 1.2.5-r9)
(42/45) Upgrading tzdata (2024b-r1 -> 2025c-r0)
(43/45) Upgrading xkbcomp (1.4.7-r0 -> 1.5.0-r0)
(44/45) Upgrading xorg-server-common (21.1.14-r0 -> 21.1.16-r0)
(45/45) Upgrading xvfb (21.1.14-r0 -> 21.1.16-r0)
Executing busybox-1.37.0-r14.trigger
Executing glib-2.82.5-r0.trigger
Executing gtk-update-icon-cache-3.24.49-r0.trigger
Executing gtk+3.0-3.24.49-r0.trigger
OK: 729 MiB in 207 packages
---> Removed intermediate container 6f856e5732a8
---> bdce0244226d
Step 3/5 : VOLUME ["/channels-dvr"]
---> Running in 636efe7ff74e
---> Removed intermediate container 636efe7ff74e
---> 1bdc63ac1173
Step 4/5 : ENTRYPOINT ["/sbin/tini", "--"]
---> Running in d30c920eac09
---> Removed intermediate container d30c920eac09
---> f6865eab15dd
Step 5/5 : CMD ./run.sh
---> Running in 58fb298f5b91
---> Removed intermediate container 58fb298f5b91
---> dfaa36611ea8
Successfully built dfaa36611ea8
Successfully tagged channels-dvr-j0e:tve
Then when deploying the image in Portainer-Stacks, you'd use this new local image like so:
services:
# 2026.01.06
# Docker Hub home for this project: https://hub.docker.com/r/fancybits/channels-dvr
channels-dvr:
image: channels-dvr-j0e:${TAG}
container_name: channels-dvr-j0e
devices:
- /dev/dri:/dev/dri
ports:
- ${HOST_PORT}:${CHANNELS_PORT}
environment:
- CHANNELS_PORT=${CHANNELS_PORT}
- TZ=${TZ}
volumes:
- ${HOST_DIR}/channels-dvr-local:/channels-dvr
- ${DVR_SHARE}:${DVR_CONTAINER_DIR}
network_mode: host
restart: unless-stopped
#volumes: # use this section if you've setup a docker volume named channels-dvr, with CIFS or NFS, to bind to /channels-dvr inside the container
#channels-dvr:
#external: ${VOL_EXTERNAL}
#name: ${VOL_NAME}
With env var overrides along these lines (adjust for your needs):
TAG=tve
HOST_PORT=8089
CHANNELS_PORT=8089
TZ=US/Mountain
HOST_DIR=/data
DVR_SHARE=/data/channels-data
DVR_CONTAINER_DIR=/data/channels-data