UniFi has the capability to port forward a port (8089) but limiting the external IPs that can access the server. I have mapped 2 of my friend's IPs to access my ChannelsDVR.
I don't want to make the setting as "Any" IP since that opens the port to everyone.
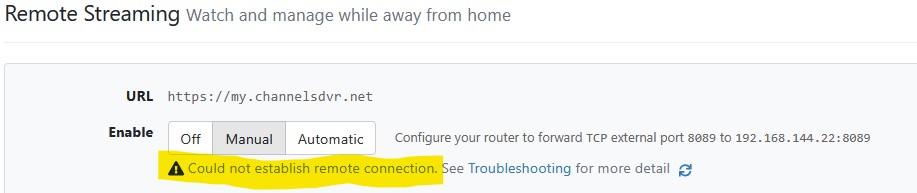
With the limited IPs for this port forward I keep getting:
"Could not connect to 655ac57xxxxx.u.channelsdvr.net. Check if the port is mapped" since the ChannelsDVR system does not get through to my server.
What is the IP/IPs that ChannelsDVR uses for the above so I can set it/them in my limited IP list?