The VNC client can be on any machine. There is some minimal configuration for the client where you'll be asked the ip:port of the server you want to connect to -- and you'd use the ip of the computer cc4c is running on, and 5900 for the port unless it was overridden during the installation.
Can the chrome browser be on any machine as well. Or, must it be on the same system which is running Channels and/or the cc4c container?
In the Docker version of cc4c, Chrome is included in the container, and is what's used.
Another cc4c in Project One-Click question — How do I change my display resolution in the VNC server?
I recall from my early days running cc4c that a higher resolution was how to eliminate black bars and a small window in Channels, but I can't figure out how to increase the resolution. I've searched online for general ways to do it in Linux, but haven't found anything that translates to this. Thank you.
(By the way, for anyone else who sees this some day, my issue with Chrome supposedly being out of date went away after I restarted either the container or Chrome (I don't recall which).)
I'd like to request some help from you on this front. I don't use this container regularly myself, so I don't have a particularly good way to test things. But, I am interested in getting the container version of cc4c in better order.
So, if you could test the following for me, I'll incorporate those changes into Project One-Click. Here's an updated stack that will allow you to change the viewport size. To implement it, stop the cc4c stack and paste in this new compose, along with adding the couple of new environment variables:
version: '3.9'
services:
cc4c:
image: fancybits/chrome-capture-for-channels:${TAG}
container_name: cc4c
command:
- sh
- -c
- |
Xvfb :99 -screen 0 1920x1080x16 &
x11vnc -display :99 -forever &
sed -i '/width: 1920/c\ width: process.env.WIDTH,' main.js;
sed -i '/height: 1080/c\ height: process.env.HEIGHT,' main.js;
sed -i '/videoBitsPerSecond/c\ videoBitsPerSecond: process.env.VIDEO,' main.js;
sed -i '/audioBitsPerSecond/c\ audioBitsPerSecond: process.env.AUDIO,' main.js;
exec node main.js
#devices:
#- /dev/dri:/dev/dri # Uncomment for Intel Quick Sync (GPU) access
ports:
- ${HOST_PORT}:5589 # cc4c proxy port
- ${HOST_VNC_PORT}:5900 # VNC port for entering credentials
environment:
- WIDTH=${WIDTH} # Desired viewport width. 1920 suggested.
- HEIGHT=${HEIGHT} # Desired viewport height. 1080 suggested.
- VIDEO=${VIDEO} # Desired video streaming rate in bps.
- AUDIO=${AUDIO} # Desired audio streaming rate in bps.
- TZ=${TZ} # Add your timezone in the Environment variables section with "name" set to TZ and "value" to your local timezone
volumes:
- cc4c:/home/chrome # Creates persistent Docker Volume in /var/lib/docker/volumes for Chrome data and main.js
restart: unless-stopped
volumes:
cc4c:
name: ${HOST_VOLUME} # The filename you'd like Docker to use for the volume.
And the sample env vars:
TAG=latest
HOST_PORT=5589
HOST_VNC_PORT=5900
WIDTH=1920
HEIGHT=1080
VIDEO=8000000
AUDIO=192000
TZ=US/Mountain
HOST_VOLUME=cc4c_config
Hi, I have been trying to get cc4c working for a while now. After scanning/reading through the 1500+ posts in the BETA: Chrome Capture for Channels feed, I'm close to giving up.
I have ordered a linkpi HDMI encoder so that I can try the ADBTuner: A "channel tuning" application for networked Google TV / Android TV devices route instead. While awaiting delivery of the linkpi device, I think I'll make another try on the cc4c today.
The cc4c container is up and running. I get the following on Port 5589:

I have added the M3U source but the windy and weatherscan channels will not play.
I haven't tried any of the other channels as I'm focusing on these to verify the installation is working.
An encoder is the way to go. cc4c seems to work fine for some folks, but encoders are totally scalable, and purpose built for this kind of thing.
I'm no expert on cc4c as I use encoders for my "daily drivers", but I do have it running, and this is the M3U I use for weatherscan:
#EXTM3U
#EXTINF:-1 channel-id="weatherscan",Weatherscan
chrome://htpc6:5589/stream?url=https://weatherscan.net
Really dumb question, but where do I paste in the new compose? I see where the environmental variables go (I think), but don't see where I'd paste the new compose
Stop the cc4c stack:
Go into the stack editor:
Replace the existing compose with the new one I posted:
Update the environment variables:
Update the stack (no need to re-pull and redeploy in this case):
That's about it for me and cc4c. I'll patiently await delivery of the HDMI encoder and focus my efforts on that method. Thanks for your help! 
Hmm, I suspect I did something wrong. I get a spinning circle in Channels, and the "connection to the tuner was lost" message. Unfortunately, I'm heading out shortly and might have limited time to troubleshoot this.
Any errors showing in the Portainer log for the cc4c container?
Here is the log when I try to tune via cc4c, select the cc4c container, and select the log icon:
#@ and then starting x11vnc via: @#
#@ @#
#@ x11vnc -rfbauth /path/to/passfile @#
#@ @#
#@ an existing ~/.vnc/passwd file from another VNC @#
#@ application will work fine too. @#
#@ @#
#@ You can also use the -passwdfile or -passwd options. @#
#@ (note -passwd is unsafe if local users are not trusted) @#
#@ @#
#@ Make sure any -rfbauth and -passwdfile password files @#
#@ cannot be read by untrusted users. @#
#@ @#
#@ Use x11vnc -usepw to automatically use your @#
#@ ~/.vnc/passwd or ~/.vnc/passwdfile password files. @#
#@ (and prompt you to create ~/.vnc/passwd if neither @#
#@ file exists.) Under -usepw, x11vnc will exit if it @#
#@ cannot find a password to use. @#
#@ @#
#@ @#
#@ Even with a password, the subsequent VNC traffic is @#
#@ sent in the clear. Consider tunnelling via ssh(1): @#
#@ @#
#@ http://www.karlrunge.com/x11vnc/#tunnelling @#
#@ @#
#@ Or using the x11vnc SSL options: -ssl and -stunnel @#
#@ @#
#@ Please Read the documentation for more info about @#
#@ passwords, security, and encryption. @#
#@ @#
#@ http://www.karlrunge.com/x11vnc/faq.html#faq-passwd @#
#@ @#
#@ To disable this warning use the -nopw option, or put @#
#@ 'nopw' on a line in your ~/.x11vncrc file. @#
#@ @#
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
###############################################################
02/08/2024 05:52:18 x11vnc version: 0.9.16 lastmod: 2019-01-05 pid: 9
02/08/2024 05:52:18 XOpenDisplay(":99") failed.
02/08/2024 05:52:18 Trying again with XAUTHLOCALHOSTNAME=localhost ...
02/08/2024 05:52:18 ***************************************
02/08/2024 05:52:18 *** XOpenDisplay failed (:99)
*** x11vnc was unable to open the X DISPLAY: ":99", it cannot continue.
*** There may be "Xlib:" error messages above with details about the failure.
Some tips and guidelines:
** An X server (the one you wish to view) must be running before x11vnc is
started: x11vnc does not start the X server. (however, see the -create
option if that is what you really want).
** You must use -display <disp>, -OR- set and export your $DISPLAY
environment variable to refer to the display of the desired X server.
- Usually the display is simply ":0" (in fact x11vnc uses this if you forget
to specify it), but in some multi-user situations it could be ":1", ":2",
or even ":137". Ask your administrator or a guru if you are having
difficulty determining what your X DISPLAY is.
** Next, you need to have sufficient permissions (Xauthority)
to connect to the X DISPLAY. Here are some Tips:
- Often, you just need to run x11vnc as the user logged into the X session.
So make sure to be that user when you type x11vnc.
- Being root is usually not enough because the incorrect MIT-MAGIC-COOKIE
file may be accessed. The cookie file contains the secret key that
allows x11vnc to connect to the desired X DISPLAY.
- You can explicitly indicate which MIT-MAGIC-COOKIE file should be used
by the -auth option, e.g.:
x11vnc -auth /home/someuser/.Xauthority -display :0
x11vnc -auth /tmp/.gdmzndVlR -display :0
you must have read permission for the auth file.
See also '-auth guess' and '-findauth' discussed below.
** If NO ONE is logged into an X session yet, but there is a greeter login
program like "gdm", "kdm", "xdm", or "dtlogin" running, you will need
to find and use the raw display manager MIT-MAGIC-COOKIE file.
Some examples for various display managers:
gdm: -auth /var/gdm/:0.Xauth
-auth /var/lib/gdm/:0.Xauth
kdm: -auth /var/lib/kdm/A:0-crWk72
-auth /var/run/xauth/A:0-crWk72
xdm: -auth /var/lib/xdm/authdir/authfiles/A:0-XQvaJk
dtlogin: -auth /var/dt/A:0-UgaaXa
Sometimes the command "ps wwwwaux | grep auth" can reveal the file location.
Starting with x11vnc 0.9.9 you can have it try to guess by using:
-auth guess
(see also the x11vnc -findauth option.)
Only root will have read permission for the file, and so x11vnc must be run
as root (or copy it). The random characters in the filenames will of course
change and the directory the cookie file resides in is system dependent.
See also: http://www.karlrunge.com/x11vnc/faq.html
Traveling today and for a while, so my access will be sporadic (but yay for Tailscale on the machine running Channels and Portainer).
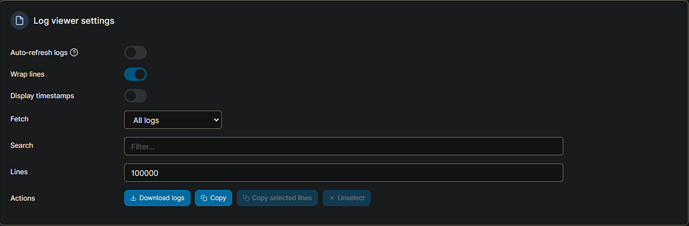
I'd like to see the complete log since spin-up, and the way I usually do that is to change the number of log lines to 100000 and turn Auto-refresh off:
This makes it easy to grab the entire log:
_XSERVTransmkdir: ERROR: euid != 0,directory /tmp/.X11-unix will not be created.
###############################################################
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
#@ @#
#@ ** WARNING ** WARNING ** WARNING ** WARNING ** @#
#@ @#
#@ YOU ARE RUNNING X11VNC WITHOUT A PASSWORD!! @#
#@ @#
#@ This means anyone with network access to this computer @#
#@ may be able to view and control your desktop. @#
#@ @#
#@ >>> If you did not mean to do this Press CTRL-C now!! <<< @#
#@ @#
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
[2024/07/31 17:03:38.723] Chrome Capture server listening on port 5589
#@ @#
#@ You can create an x11vnc password file by running: @#
#@ @#
#@ x11vnc -storepasswd password /path/to/passfile @#
#@ or x11vnc -storepasswd /path/to/passfile @#
#@ or x11vnc -storepasswd @#
#@ @#
#@ (the last one will use ~/.vnc/passwd) @#
#@ @#
#@ and then starting x11vnc via: @#
#@ @#
#@ x11vnc -rfbauth /path/to/passfile @#
#@ @#
#@ an existing ~/.vnc/passwd file from another VNC @#
#@ application will work fine too. @#
#@ @#
#@ You can also use the -passwdfile or -passwd options. @#
#@ (note -passwd is unsafe if local users are not trusted) @#
#@ @#
#@ Make sure any -rfbauth and -passwdfile password files @#
#@ cannot be read by untrusted users. @#
#@ @#
#@ Use x11vnc -usepw to automatically use your @#
#@ ~/.vnc/passwd or ~/.vnc/passwdfile password files. @#
#@ (and prompt you to create ~/.vnc/passwd if neither @#
#@ file exists.) Under -usepw, x11vnc will exit if it @#
#@ cannot find a password to use. @#
#@ @#
#@ @#
#@ Even with a password, the subsequent VNC traffic is @#
#@ sent in the clear. Consider tunnelling via ssh(1): @#
#@ @#
#@ http://www.karlrunge.com/x11vnc/#tunnelling @#
#@ @#
#@ Or using the x11vnc SSL options: -ssl and -stunnel @#
#@ @#
#@ Please Read the documentation for more info about @#
#@ passwords, security, and encryption. @#
#@ @#
#@ http://www.karlrunge.com/x11vnc/faq.html#faq-passwd @#
#@ @#
#@ To disable this warning use the -nopw option, or put @#
#@ 'nopw' on a line in your ~/.x11vncrc file. @#
#@ @#
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
###############################################################
31/07/2024 17:03:39 x11vnc version: 0.9.16 lastmod: 2019-01-05 pid: 9
31/07/2024 17:03:39 Using X display :99
31/07/2024 17:03:39 rootwin: 0x400 reswin: 0x200001 dpy: 0xf4025800
31/07/2024 17:03:39
31/07/2024 17:03:39 ------------------ USEFUL INFORMATION ------------------
31/07/2024 17:03:39 X DAMAGE available on display, using it for polling hints.
31/07/2024 17:03:39 To disable this behavior use: '-noxdamage'
31/07/2024 17:03:39
31/07/2024 17:03:39 Most compositing window managers like 'compiz' or 'beryl'
31/07/2024 17:03:39 cause X DAMAGE to fail, and so you may not see any screen
31/07/2024 17:03:39 updates via VNC. Either disable 'compiz' (recommended) or
31/07/2024 17:03:39 supply the x11vnc '-noxdamage' command line option.
31/07/2024 17:03:39
31/07/2024 17:03:39 Wireframing: -wireframe mode is in effect for window moves.
31/07/2024 17:03:39 If this yields undesired behavior (poor response, painting
31/07/2024 17:03:39 errors, etc) it may be disabled:
31/07/2024 17:03:39 - use '-nowf' to disable wireframing completely.
31/07/2024 17:03:39 - use '-nowcr' to disable the Copy Rectangle after the
31/07/2024 17:03:39 moved window is released in the new position.
31/07/2024 17:03:39 Also see the -help entry for tuning parameters.
31/07/2024 17:03:39 You can press 3 Alt_L's (Left "Alt" key) in a row to
31/07/2024 17:03:39 repaint the screen, also see the -fixscreen option for
31/07/2024 17:03:39 periodic repaints.
31/07/2024 17:03:39
31/07/2024 17:03:39 XFIXES available on display, resetting cursor mode
31/07/2024 17:03:39 to: '-cursor most'.
31/07/2024 17:03:39 to disable this behavior use: '-cursor arrow'
31/07/2024 17:03:39 or '-noxfixes'.
31/07/2024 17:03:39 using XFIXES for cursor drawing.
31/07/2024 17:03:39 GrabServer control via XTEST.
31/07/2024 17:03:39
31/07/2024 17:03:39 Scroll Detection: -scrollcopyrect mode is in effect to
31/07/2024 17:03:39 use RECORD extension to try to detect scrolling windows
31/07/2024 17:03:39 (induced by either user keystroke or mouse input).
31/07/2024 17:03:39 If this yields undesired behavior (poor response, painting
31/07/2024 17:03:39 errors, etc) it may be disabled via: '-noscr'
31/07/2024 17:03:39 Also see the -help entry for tuning parameters.
31/07/2024 17:03:39 You can press 3 Alt_L's (Left "Alt" key) in a row to
31/07/2024 17:03:39 repaint the screen, also see the -fixscreen option for
31/07/2024 17:03:39 periodic repaints.
31/07/2024 17:03:39
31/07/2024 17:03:39 XKEYBOARD: number of keysyms per keycode 7 is greater
31/07/2024 17:03:39 than 4 and 51 keysyms are mapped above 4.
31/07/2024 17:03:39 Automatically switching to -xkb mode.
31/07/2024 17:03:39 If this makes the key mapping worse you can
31/07/2024 17:03:39 disable it with the "-noxkb" option.
31/07/2024 17:03:39 Also, remember "-remap DEAD" for accenting characters.
31/07/2024 17:03:39
31/07/2024 17:03:39 X FBPM extension not supported.
Xlib: extension "DPMS" missing on display ":99".
31/07/2024 17:03:39 X display is not capable of DPMS.
31/07/2024 17:03:39 --------------------------------------------------------
31/07/2024 17:03:39
31/07/2024 17:03:39 Default visual ID: 0x21
31/07/2024 17:03:39 Read initial data from X display into framebuffer.
31/07/2024 17:03:39 initialize_screen: fb_depth/fb_bpp/fb_Bpl 16/16/3840
31/07/2024 17:03:39
31/07/2024 17:03:39 X display :99 is 16bpp depth=16 true color
31/07/2024 17:03:39
31/07/2024 17:03:39 Autoprobing TCP port
31/07/2024 17:03:39 Autoprobing selected TCP port 5900
31/07/2024 17:03:39 Autoprobing TCP6 port
31/07/2024 17:03:39 Autoprobing selected TCP6 port 5900
31/07/2024 17:03:39 listen6: bind: Address already in use
31/07/2024 17:03:39 Not listening on IPv6 interface.
31/07/2024 17:03:39
31/07/2024 17:03:39 Xinerama is present and active (e.g. multi-head).
31/07/2024 17:03:39 Xinerama: number of sub-screens: 1
31/07/2024 17:03:39 Xinerama: no blackouts needed (only one sub-screen)
31/07/2024 17:03:39
31/07/2024 17:03:39 fb read rate: 3490 MB/sec
31/07/2024 17:03:39 fast read: reset -wait ms to: 10
31/07/2024 17:03:39 fast read: reset -defer ms to: 10
31/07/2024 17:03:39 The X server says there are 10 mouse buttons.
31/07/2024 17:03:39 screen setup finished.
31/07/2024 17:03:39
31/07/2024 17:03:39 WARNING: You are running x11vnc WITHOUT a password. See
31/07/2024 17:03:39 WARNING: the warning message printed above for more info.
31/07/2024 17:03:39
The VNC desktop is: 4d8b85dfba32:0
0
******************************************************************************
Have you tried the x11vnc '-ncache' VNC client-side pixel caching feature yet?
The scheme stores pixel data offscreen on the VNC viewer side for faster
retrieval. It should work with any VNC viewer. Try it by running:
x11vnc -ncache 10 ...
One can also add -ncache_cr for smooth 'copyrect' window motion.
More info: http://www.karlrunge.com/x11vnc/faq.html#faq-client-caching
[2024/07/31 17:04:11.699] streaming https://watch.frndlytv.com/channel/live/lifetime
[2024/07/31 17:04:13.003] failed to stream https://watch.frndlytv.com/channel/live/lifetime ProtocolError: Protocol error (Browser.setWindowBounds): Invalid parameters Failed to deserialize params.bounds.height - BINDINGS: int32 value expected at position 44
at new Callback (/home/chrome/node_modules/puppeteer-core/lib/cjs/puppeteer/common/Connection.js:62:35)
at CallbackRegistry.create (/home/chrome/node_modules/puppeteer-core/lib/cjs/puppeteer/common/Connection.js:108:26)
at Connection._rawSend (/home/chrome/node_modules/puppeteer-core/lib/cjs/puppeteer/common/Connection.js:224:26)
at CDPSessionImpl.send (/home/chrome/node_modules/puppeteer-core/lib/cjs/puppeteer/common/Connection.js:433:78)
at /home/chrome/main.js:340:21
at process.processTicksAndRejections (node:internal/process/task_queues:95:5)
[2024/07/31 17:04:45.392] GET /stream?url=https://watch.frndlytv.com/channel/live/lifetime from ::ffff:100.101.18.9 responded 200 in 452.690 ms
[2024/07/31 17:04:45.408] finished https://watch.frndlytv.com/channel/live/lifetime
Got this working by logging in via Real VNC... however, the channels open up within a box (letterboxed/pillarboxed all the way around - not 1920x1080... and I used your new compose above)... any way to fix that? In other words, channels aren't displaying full-screen.
Also... is there a way to edit main.js for this? I have a command in my other install of main.js that can unmute channels on Peacock... would like to run that here too.
You should be able to edit the main.js in the location where Docker stores its Volumes, which is:
/var/lib/docker/volumes
The cc4c data would then be under:
cc4c_config/_data
If going fullscreen when you VNC-in isn't working, you could try adding this:
I'd suggest restarting the container after making any changes to main.js.
You may also want to take a look at the args this guy is using, combined with enabling Intel Quick Sync (assuming you have an Intel video chip) via /dev/dri:
Thanks for the reply! I think the issue is I'm using a UGreen NAS and it won't let me access any of those files... at least not that I can figure out from File Manager or Finder on Mac. It'll only show me the folders that have been shared externally... I'm trying to figure out how to get to those to try and tackle this.
We should be able to make just about any change to main.js through the Docker Compose -- which is really better anyway. Besides the "fullscreen" line, what else would you like to insert, and where in the code does it need to go?
The UGreen has Intel QuickSync, so I've turned that on, but I am still getting this massive letterboxing issue. I can't figure out why.
As for the other issue with main.js... my original install on a Mac Mini (which I'm trying to move away from since this UGreen has massive specs and should handle CC4C fine... ) ... when viewing channels on Peacock via CC4C, those channels were loading muted by default (this is something Peacock annoyingly does). To remove that, I had to follow these instructions adding to main.js:
https://community.getchannels.com/t/beta-chrome-capture-for-channels/36667/1362?u=radioboy
Now, if there's a way to do that through Docker compose, this is going to get really good really fast 
Here's what I get when using those log settings:
###############################################################
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
#@ @#
#@ ** WARNING ** WARNING ** WARNING ** WARNING ** @#
#@ @#
#@ YOU ARE RUNNING X11VNC WITHOUT A PASSWORD!! @#
#@ @#
#@ This means anyone with network access to this computer @#
#@ may be able to view and control your desktop. @#
#@ @#
#@ >>> If you did not mean to do this Press CTRL-C now!! <<< @#
#@ @#
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
_XSERVTransmkdir: ERROR: euid != 0,directory /tmp/.X11-unix will not be created.
[2024/08/01 11:23:26.130] Chrome Capture server listening on port 5589
#@ @#
#@ You can create an x11vnc password file by running: @#
#@ @#
#@ x11vnc -storepasswd password /path/to/passfile @#
#@ or x11vnc -storepasswd /path/to/passfile @#
#@ or x11vnc -storepasswd @#
#@ @#
#@ (the last one will use ~/.vnc/passwd) @#
#@ @#
#@ and then starting x11vnc via: @#
#@ @#
#@ x11vnc -rfbauth /path/to/passfile @#
#@ @#
#@ an existing ~/.vnc/passwd file from another VNC @#
#@ application will work fine too. @#
#@ @#
#@ You can also use the -passwdfile or -passwd options. @#
#@ (note -passwd is unsafe if local users are not trusted) @#
#@ @#
#@ Make sure any -rfbauth and -passwdfile password files @#
#@ cannot be read by untrusted users. @#
#@ @#
#@ Use x11vnc -usepw to automatically use your @#
#@ ~/.vnc/passwd or ~/.vnc/passwdfile password files. @#
#@ (and prompt you to create ~/.vnc/passwd if neither @#
#@ file exists.) Under -usepw, x11vnc will exit if it @#
#@ cannot find a password to use. @#
#@ @#
#@ @#
#@ Even with a password, the subsequent VNC traffic is @#
#@ sent in the clear. Consider tunnelling via ssh(1): @#
#@ @#
#@ http://www.karlrunge.com/x11vnc/#tunnelling @#
#@ @#
#@ Or using the x11vnc SSL options: -ssl and -stunnel @#
#@ @#
#@ Please Read the documentation for more info about @#
#@ passwords, security, and encryption. @#
#@ @#
#@ http://www.karlrunge.com/x11vnc/faq.html#faq-passwd @#
#@ @#
#@ To disable this warning use the -nopw option, or put @#
#@ 'nopw' on a line in your ~/.x11vncrc file. @#
#@ @#
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
###############################################################
01/08/2024 11:23:26 x11vnc version: 0.9.16 lastmod: 2019-01-05 pid: 9
01/08/2024 11:23:26 Using X display :99
01/08/2024 11:23:26 rootwin: 0x400 reswin: 0x200001 dpy: 0x5594d7f0
01/08/2024 11:23:26
01/08/2024 11:23:26 ------------------ USEFUL INFORMATION ------------------
01/08/2024 11:23:26 X DAMAGE available on display, using it for polling hints.
01/08/2024 11:23:26 To disable this behavior use: '-noxdamage'
01/08/2024 11:23:26
01/08/2024 11:23:26 Most compositing window managers like 'compiz' or 'beryl'
01/08/2024 11:23:26 cause X DAMAGE to fail, and so you may not see any screen
01/08/2024 11:23:26 updates via VNC. Either disable 'compiz' (recommended) or
01/08/2024 11:23:26 supply the x11vnc '-noxdamage' command line option.
01/08/2024 11:23:26
01/08/2024 11:23:26 Wireframing: -wireframe mode is in effect for window moves.
01/08/2024 11:23:26 If this yields undesired behavior (poor response, painting
01/08/2024 11:23:26 errors, etc) it may be disabled:
01/08/2024 11:23:26 - use '-nowf' to disable wireframing completely.
01/08/2024 11:23:26 - use '-nowcr' to disable the Copy Rectangle after the
01/08/2024 11:23:26 moved window is released in the new position.
01/08/2024 11:23:26 Also see the -help entry for tuning parameters.
01/08/2024 11:23:26 You can press 3 Alt_L's (Left "Alt" key) in a row to
01/08/2024 11:23:26 repaint the screen, also see the -fixscreen option for
01/08/2024 11:23:26 periodic repaints.
01/08/2024 11:23:26
01/08/2024 11:23:26 XFIXES available on display, resetting cursor mode
01/08/2024 11:23:26 to: '-cursor most'.
01/08/2024 11:23:26 to disable this behavior use: '-cursor arrow'
01/08/2024 11:23:26 or '-noxfixes'.
01/08/2024 11:23:26 using XFIXES for cursor drawing.
01/08/2024 11:23:26 GrabServer control via XTEST.
01/08/2024 11:23:26
01/08/2024 11:23:26 Scroll Detection: -scrollcopyrect mode is in effect to
01/08/2024 11:23:26 use RECORD extension to try to detect scrolling windows
01/08/2024 11:23:26 (induced by either user keystroke or mouse input).
01/08/2024 11:23:26 If this yields undesired behavior (poor response, painting
01/08/2024 11:23:26 errors, etc) it may be disabled via: '-noscr'
01/08/2024 11:23:26 Also see the -help entry for tuning parameters.
01/08/2024 11:23:26 You can press 3 Alt_L's (Left "Alt" key) in a row to
01/08/2024 11:23:26 repaint the screen, also see the -fixscreen option for
01/08/2024 11:23:26 periodic repaints.
01/08/2024 11:23:26
01/08/2024 11:23:26 XKEYBOARD: number of keysyms per keycode 7 is greater
01/08/2024 11:23:26 than 4 and 51 keysyms are mapped above 4.
01/08/2024 11:23:26 Automatically switching to -xkb mode.
01/08/2024 11:23:26 If this makes the key mapping worse you can
01/08/2024 11:23:26 disable it with the "-noxkb" option.
01/08/2024 11:23:26 Also, remember "-remap DEAD" for accenting characters.
01/08/2024 11:23:26
01/08/2024 11:23:26 X FBPM extension not supported.
Xlib: extension "DPMS" missing on display ":99".
01/08/2024 11:23:26 X display is not capable of DPMS.
01/08/2024 11:23:26 --------------------------------------------------------
01/08/2024 11:23:26
01/08/2024 11:23:26 Default visual ID: 0x21
01/08/2024 11:23:26 Read initial data from X display into framebuffer.
01/08/2024 11:23:26 initialize_screen: fb_depth/fb_bpp/fb_Bpl 16/16/3840
01/08/2024 11:23:26
01/08/2024 11:23:26 X display :99 is 16bpp depth=16 true color
01/08/2024 11:23:26
01/08/2024 11:23:26 Autoprobing TCP port
01/08/2024 11:23:26 Autoprobing selected TCP port 5900
01/08/2024 11:23:26 Autoprobing TCP6 port
01/08/2024 11:23:26 Autoprobing selected TCP6 port 5900
01/08/2024 11:23:26 listen6: bind: Address already in use
01/08/2024 11:23:26 Not listening on IPv6 interface.
01/08/2024 11:23:26
01/08/2024 11:23:26 Xinerama is present and active (e.g. multi-head).
01/08/2024 11:23:26 Xinerama: number of sub-screens: 1
01/08/2024 11:23:26 Xinerama: no blackouts needed (only one sub-screen)
01/08/2024 11:23:26
01/08/2024 11:23:26 fb read rate: 1546 MB/sec
01/08/2024 11:23:26 fast read: reset -wait ms to: 10
01/08/2024 11:23:26 fast read: reset -defer ms to: 10
01/08/2024 11:23:26 The X server says there are 10 mouse buttons.
01/08/2024 11:23:26 screen setup finished.
01/08/2024 11:23:26
01/08/2024 11:23:26 WARNING: You are running x11vnc WITHOUT a password. See
01/08/2024 11:23:26 WARNING: the warning message printed above for more info.
01/08/2024 11:23:26
The VNC desktop is: 4327c487ef12:0
0
******************************************************************************
Have you tried the x11vnc '-ncache' VNC client-side pixel caching feature yet?
The scheme stores pixel data offscreen on the VNC viewer side for faster
retrieval. It should work with any VNC viewer. Try it by running:
x11vnc -ncache 10 ...
One can also add -ncache_cr for smooth 'copyrect' window motion.
More info: http://www.karlrunge.com/x11vnc/faq.html#faq-client-caching
/home/chrome/node_modules/puppeteer-core/lib/cjs/puppeteer/node/ProductLauncher.js:153
throw new Errors_js_1.TimeoutError(error.message);
^
TimeoutError: Timed out after 30000 ms while waiting for the WS endpoint URL to appear in stdout!
at ChromeLauncher.launch (/home/chrome/node_modules/puppeteer-core/lib/cjs/puppeteer/node/ProductLauncher.js:153:23)
Node.js v18.16.0
(EE)
Fatal server error:
(EE) Server is already active for display 99
If this server is no longer running, remove /tmp/.X99-lock
and start again.
(EE)
###############################################################
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
#@ @#
#@ ** WARNING ** WARNING ** WARNING ** WARNING ** @#
#@ @#
#@ YOU ARE RUNNING X11VNC WITHOUT A PASSWORD!! @#
#@ @#
#@ This means anyone with network access to this computer @#
#@ may be able to view and control your desktop. @#
#@ @#
#@ >>> If you did not mean to do this Press CTRL-C now!! <<< @#
#@ @#
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
[2024/08/01 11:24:25.642] Chrome Capture server listening on port 5589
#@ @#
#@ You can create an x11vnc password file by running: @#
#@ @#
#@ x11vnc -storepasswd password /path/to/passfile @#
#@ or x11vnc -storepasswd /path/to/passfile @#
#@ or x11vnc -storepasswd @#
#@ @#
#@ (the last one will use ~/.vnc/passwd) @#
#@ @#
#@ and then starting x11vnc via: @#
#@ @#
#@ x11vnc -rfbauth /path/to/passfile @#
#@ @#
#@ an existing ~/.vnc/passwd file from another VNC @#
#@ application will work fine too. @#
#@ @#
#@ You can also use the -passwdfile or -passwd options. @#
#@ (note -passwd is unsafe if local users are not trusted) @#
#@ @#
#@ Make sure any -rfbauth and -passwdfile password files @#
#@ cannot be read by untrusted users. @#
#@ @#
#@ Use x11vnc -usepw to automatically use your @#
#@ ~/.vnc/passwd or ~/.vnc/passwdfile password files. @#
#@ (and prompt you to create ~/.vnc/passwd if neither @#
#@ file exists.) Under -usepw, x11vnc will exit if it @#
#@ cannot find a password to use. @#
#@ @#
#@ @#
#@ Even with a password, the subsequent VNC traffic is @#
#@ sent in the clear. Consider tunnelling via ssh(1): @#
#@ @#
#@ http://www.karlrunge.com/x11vnc/#tunnelling @#
#@ @#
#@ Or using the x11vnc SSL options: -ssl and -stunnel @#
#@ @#
#@ Please Read the documentation for more info about @#
#@ passwords, security, and encryption. @#
#@ @#
#@ http://www.karlrunge.com/x11vnc/faq.html#faq-passwd @#
#@ @#
#@ To disable this warning use the -nopw option, or put @#
#@ 'nopw' on a line in your ~/.x11vncrc file. @#
#@ @#
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
###############################################################
01/08/2024 11:24:25 x11vnc version: 0.9.16 lastmod: 2019-01-05 pid: 9
01/08/2024 11:24:25 XOpenDisplay(":99") failed.
01/08/2024 11:24:25 Trying again with XAUTHLOCALHOSTNAME=localhost ...
01/08/2024 11:24:25 ***************************************
01/08/2024 11:24:25 *** XOpenDisplay failed (:99)
*** x11vnc was unable to open the X DISPLAY: ":99", it cannot continue.
*** There may be "Xlib:" error messages above with details about the failure.
Some tips and guidelines:
** An X server (the one you wish to view) must be running before x11vnc is
started: x11vnc does not start the X server. (however, see the -create
option if that is what you really want).
** You must use -display <disp>, -OR- set and export your $DISPLAY
environment variable to refer to the display of the desired X server.
- Usually the display is simply ":0" (in fact x11vnc uses this if you forget
to specify it), but in some multi-user situations it could be ":1", ":2",
or even ":137". Ask your administrator or a guru if you are having
difficulty determining what your X DISPLAY is.
** Next, you need to have sufficient permissions (Xauthority)
to connect to the X DISPLAY. Here are some Tips:
- Often, you just need to run x11vnc as the user logged into the X session.
So make sure to be that user when you type x11vnc.
- Being root is usually not enough because the incorrect MIT-MAGIC-COOKIE
file may be accessed. The cookie file contains the secret key that
allows x11vnc to connect to the desired X DISPLAY.
- You can explicitly indicate which MIT-MAGIC-COOKIE file should be used
by the -auth option, e.g.:
x11vnc -auth /home/someuser/.Xauthority -display :0
x11vnc -auth /tmp/.gdmzndVlR -display :0
you must have read permission for the auth file.
See also '-auth guess' and '-findauth' discussed below.
** If NO ONE is logged into an X session yet, but there is a greeter login
program like "gdm", "kdm", "xdm", or "dtlogin" running, you will need
to find and use the raw display manager MIT-MAGIC-COOKIE file.
Some examples for various display managers:
gdm: -auth /var/gdm/:0.Xauth
-auth /var/lib/gdm/:0.Xauth
kdm: -auth /var/lib/kdm/A:0-crWk72
-auth /var/run/xauth/A:0-crWk72
xdm: -auth /var/lib/xdm/authdir/authfiles/A:0-XQvaJk
dtlogin: -auth /var/dt/A:0-UgaaXa
Sometimes the command "ps wwwwaux | grep auth" can reveal the file location.
Starting with x11vnc 0.9.9 you can have it try to guess by using:
-auth guess
(see also the x11vnc -findauth option.)
Only root will have read permission for the file, and so x11vnc must be run
as root (or copy it). The random characters in the filenames will of course
change and the directory the cookie file resides in is system dependent.
See also: http://www.karlrunge.com/x11vnc/faq.html
(EE)
Fatal server error:
(EE) Server is already active for display 99
If this server is no longer running, remove /tmp/.X99-lock
and start again.
(EE)
###############################################################
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
#@ @#
#@ ** WARNING ** WARNING ** WARNING ** WARNING ** @#
#@ @#
#@ YOU ARE RUNNING X11VNC WITHOUT A PASSWORD!! @#
#@ @#
#@ This means anyone with network access to this computer @#
#@ may be able to view and control your desktop. @#
#@ @#
#@ >>> If you did not mean to do this Press CTRL-C now!! <<< @#
#@ @#
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
#@ @#
#@ You can create an x11vnc password file by running: @#
#@ @#
#@ x11vnc -storepasswd password /path/to/passfile @#
#@ or x11vnc -storepasswd /path/to/passfile @#
#@ or x11vnc -storepasswd @#
#@ @#
#@ (the last one will use ~/.vnc/passwd) @#
#@ @#
#@ and then starting x11vnc via: @#
#@ @#
#@ x11vnc -rfbauth /path/to/passfile @#
#@ @#
#@ an existing ~/.vnc/passwd file from another VNC @#
#@ application will work fine too. @#
#@ @#
#@ You can also use the -passwdfile or -passwd options. @#
#@ (note -passwd is unsafe if local users are not trusted) @#
#@ @#
#@ Make sure any -rfbauth and -passwdfile password files @#
#@ cannot be read by untrusted users. @#
#@ @#
#@ Use x11vnc -usepw to automatically use your @#
#@ ~/.vnc/passwd or ~/.vnc/passwdfile password files. @#
#@ (and prompt you to create ~/.vnc/passwd if neither @#
#@ file exists.) Under -usepw, x11vnc will exit if it @#
#@ cannot find a password to use. @#
#@ @#
#@ @#
#@ Even with a password, the subsequent VNC traffic is @#
#@ sent in the clear. Consider tunnelling via ssh(1): @#
#@ @#
#@ http://www.karlrunge.com/x11vnc/#tunnelling @#
#@ @#
#@ Or using the x11vnc SSL options: -ssl and -stunnel @#
#@ @#
#@ Please Read the documentation for more info about @#
#@ passwords, security, and encryption. @#
#@ @#
#@ http://www.karlrunge.com/x11vnc/faq.html#faq-passwd @#
#@ @#
#@ To disable this warning use the -nopw option, or put @#
#@ 'nopw' on a line in your ~/.x11vncrc file. @#
#@ @#
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
###############################################################
01/08/2024 15:23:38 x11vnc version: 0.9.16 lastmod: 2019-01-05 pid: 9
01/08/2024 15:23:38 XOpenDisplay(":99") failed.
01/08/2024 15:23:38 Trying again with XAUTHLOCALHOSTNAME=localhost ...
01/08/2024 15:23:38 ***************************************
01/08/2024 15:23:38 *** XOpenDisplay failed (:99)
*** x11vnc was unable to open the X DISPLAY: ":99", it cannot continue.
*** There may be "Xlib:" error messages above with details about the failure.
Some tips and guidelines:
** An X server (the one you wish to view) must be running before x11vnc is
started: x11vnc does not start the X server. (however, see the -create
option if that is what you really want).
** You must use -display <disp>, -OR- set and export your $DISPLAY
environment variable to refer to the display of the desired X server.
- Usually the display is simply ":0" (in fact x11vnc uses this if you forget
to specify it), but in some multi-user situations it could be ":1", ":2",
or even ":137". Ask your administrator or a guru if you are having
difficulty determining what your X DISPLAY is.
** Next, you need to have sufficient permissions (Xauthority)
to connect to the X DISPLAY. Here are some Tips:
- Often, you just need to run x11vnc as the user logged into the X session.
So make sure to be that user when you type x11vnc.
- Being root is usually not enough because the incorrect MIT-MAGIC-COOKIE
file may be accessed. The cookie file contains the secret key that
allows x11vnc to connect to the desired X DISPLAY.
- You can explicitly indicate which MIT-MAGIC-COOKIE file should be used
by the -auth option, e.g.:
x11vnc -auth /home/someuser/.Xauthority -display :0
x11vnc -auth /tmp/.gdmzndVlR -display :0
you must have read permission for the auth file.
See also '-auth guess' and '-findauth' discussed below.
** If NO ONE is logged into an X session yet, but there is a greeter login
program like "gdm", "kdm", "xdm", or "dtlogin" running, you will need
to find and use the raw display manager MIT-MAGIC-COOKIE file.
Some examples for various display managers:
gdm: -auth /var/gdm/:0.Xauth
-auth /var/lib/gdm/:0.Xauth
kdm: -auth /var/lib/kdm/A:0-crWk72
-auth /var/run/xauth/A:0-crWk72
xdm: -auth /var/lib/xdm/authdir/authfiles/A:0-XQvaJk
dtlogin: -auth /var/dt/A:0-UgaaXa
Sometimes the command "ps wwwwaux | grep auth" can reveal the file location.
Starting with x11vnc 0.9.9 you can have it try to guess by using:
-auth guess
(see also the x11vnc -findauth option.)
Only root will have read permission for the file, and so x11vnc must be run
as root (or copy it). The random characters in the filenames will of course
change and the directory the cookie file resides in is system dependent.
See also: http://www.karlrunge.com/x11vnc/faq.html
[2024/08/01 15:23:39.294] Chrome Capture server listening on port 5589
/home/chrome/node_modules/@puppeteer/browsers/lib/cjs/launch.js:259
reject(new Error([
^
Error: Failed to launch the browser process! undefined
[20:42:0802/055212.844406:ERROR:bus.cc(399)] Failed to connect to the bus: Failed to connect to socket /run/dbus/system_bus_socket: No such file or directory
[20:20:0802/055212.887710:ERROR:ozone_platform_x11.cc(239)] Missing X server or $DISPLAY
[20:20:0802/055212.887738:ERROR:env.cc(255)] The platform failed to initialize. Exiting.
TROUBLESHOOTING: https://pptr.dev/troubleshooting
at ChildProcess.onClose (/home/chrome/node_modules/@puppeteer/browsers/lib/cjs/launch.js:259:24)
at ChildProcess.emit (node:events:525:35)
at ChildProcess._handle.onexit (node:internal/child_process:291:12)
Node.js v18.16.0
(EE)
Fatal server error:
(EE) Server is already active for display 99
If this server is no longer running, remove /tmp/.X99-lock
and start again.
(EE)
###############################################################
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
#@ @#
#@ ** WARNING ** WARNING ** WARNING ** WARNING ** @#
#@ @#
#@ YOU ARE RUNNING X11VNC WITHOUT A PASSWORD!! @#
#@ @#
#@ This means anyone with network access to this computer @#
#@ may be able to view and control your desktop. @#
#@ @#
#@ >>> If you did not mean to do this Press CTRL-C now!! <<< @#
#@ @#
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
[2024/08/02 05:52:13.904] Chrome Capture server listening on port 5589
#@ @#
#@ You can create an x11vnc password file by running: @#
#@ @#
#@ x11vnc -storepasswd password /path/to/passfile @#
#@ or x11vnc -storepasswd /path/to/passfile @#
#@ or x11vnc -storepasswd @#
#@ @#
#@ (the last one will use ~/.vnc/passwd) @#
#@ @#
#@ and then starting x11vnc via: @#
#@ @#
#@ x11vnc -rfbauth /path/to/passfile @#
#@ @#
#@ an existing ~/.vnc/passwd file from another VNC @#
#@ application will work fine too. @#
#@ @#
#@ You can also use the -passwdfile or -passwd options. @#
#@ (note -passwd is unsafe if local users are not trusted) @#
#@ @#
#@ Make sure any -rfbauth and -passwdfile password files @#
#@ cannot be read by untrusted users. @#
#@ @#
#@ Use x11vnc -usepw to automatically use your @#
#@ ~/.vnc/passwd or ~/.vnc/passwdfile password files. @#
#@ (and prompt you to create ~/.vnc/passwd if neither @#
#@ file exists.) Under -usepw, x11vnc will exit if it @#
#@ cannot find a password to use. @#
#@ @#
#@ @#
#@ Even with a password, the subsequent VNC traffic is @#
#@ sent in the clear. Consider tunnelling via ssh(1): @#
#@ @#
#@ http://www.karlrunge.com/x11vnc/#tunnelling @#
#@ @#
#@ Or using the x11vnc SSL options: -ssl and -stunnel @#
#@ @#
#@ Please Read the documentation for more info about @#
#@ passwords, security, and encryption. @#
#@ @#
#@ http://www.karlrunge.com/x11vnc/faq.html#faq-passwd @#
#@ @#
#@ To disable this warning use the -nopw option, or put @#
#@ 'nopw' on a line in your ~/.x11vncrc file. @#
#@ @#
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
###############################################################
02/08/2024 05:52:14 x11vnc version: 0.9.16 lastmod: 2019-01-05 pid: 9
02/08/2024 05:52:14 XOpenDisplay(":99") failed.
02/08/2024 05:52:14 Trying again with XAUTHLOCALHOSTNAME=localhost ...
02/08/2024 05:52:14 ***************************************
02/08/2024 05:52:14 *** XOpenDisplay failed (:99)
*** x11vnc was unable to open the X DISPLAY: ":99", it cannot continue.
*** There may be "Xlib:" error messages above with details about the failure.
Some tips and guidelines:
** An X server (the one you wish to view) must be running before x11vnc is
started: x11vnc does not start the X server. (however, see the -create
option if that is what you really want).
** You must use -display <disp>, -OR- set and export your $DISPLAY
environment variable to refer to the display of the desired X server.
- Usually the display is simply ":0" (in fact x11vnc uses this if you forget
to specify it), but in some multi-user situations it could be ":1", ":2",
or even ":137". Ask your administrator or a guru if you are having
difficulty determining what your X DISPLAY is.
** Next, you need to have sufficient permissions (Xauthority)
to connect to the X DISPLAY. Here are some Tips:
- Often, you just need to run x11vnc as the user logged into the X session.
So make sure to be that user when you type x11vnc.
- Being root is usually not enough because the incorrect MIT-MAGIC-COOKIE
file may be accessed. The cookie file contains the secret key that
allows x11vnc to connect to the desired X DISPLAY.
- You can explicitly indicate which MIT-MAGIC-COOKIE file should be used
by the -auth option, e.g.:
x11vnc -auth /home/someuser/.Xauthority -display :0
x11vnc -auth /tmp/.gdmzndVlR -display :0
you must have read permission for the auth file.
See also '-auth guess' and '-findauth' discussed below.
** If NO ONE is logged into an X session yet, but there is a greeter login
program like "gdm", "kdm", "xdm", or "dtlogin" running, you will need
to find and use the raw display manager MIT-MAGIC-COOKIE file.
Some examples for various display managers:
gdm: -auth /var/gdm/:0.Xauth
-auth /var/lib/gdm/:0.Xauth
kdm: -auth /var/lib/kdm/A:0-crWk72
-auth /var/run/xauth/A:0-crWk72
xdm: -auth /var/lib/xdm/authdir/authfiles/A:0-XQvaJk
dtlogin: -auth /var/dt/A:0-UgaaXa
Sometimes the command "ps wwwwaux | grep auth" can reveal the file location.
Starting with x11vnc 0.9.9 you can have it try to guess by using:
-auth guess
(see also the x11vnc -findauth option.)
Only root will have read permission for the file, and so x11vnc must be run
as root (or copy it). The random characters in the filenames will of course
change and the directory the cookie file resides in is system dependent.
See also: http://www.karlrunge.com/x11vnc/faq.html
/home/chrome/node_modules/@puppeteer/browsers/lib/cjs/launch.js:259
reject(new Error([
^
Error: Failed to launch the browser process! undefined
[20:42:0802/055217.080971:ERROR:bus.cc(399)] Failed to connect to the bus: Failed to connect to socket /run/dbus/system_bus_socket: No such file or directory
[20:20:0802/055217.103154:ERROR:ozone_platform_x11.cc(239)] Missing X server or $DISPLAY
[20:20:0802/055217.103168:ERROR:env.cc(255)] The platform failed to initialize. Exiting.
TROUBLESHOOTING: https://pptr.dev/troubleshooting
at ChildProcess.onClose (/home/chrome/node_modules/@puppeteer/browsers/lib/cjs/launch.js:259:24)
at ChildProcess.emit (node:events:525:35)
at ChildProcess._handle.onexit (node:internal/child_process:291:12)
Node.js v18.16.0
(EE)
Fatal server error:
(EE) Server is already active for display 99
If this server is no longer running, remove /tmp/.X99-lock
and start again.
(EE)
###############################################################
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
#@ @#
#@ ** WARNING ** WARNING ** WARNING ** WARNING ** @#
#@ @#
#@ YOU ARE RUNNING X11VNC WITHOUT A PASSWORD!! @#
#@ @#
#@ This means anyone with network access to this computer @#
#@ may be able to view and control your desktop. @#
#@ @#
#@ >>> If you did not mean to do this Press CTRL-C now!! <<< @#
#@ @#
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
[2024/08/02 05:52:18.195] Chrome Capture server listening on port 5589
#@ @#
#@ You can create an x11vnc password file by running: @#
#@ @#
#@ x11vnc -storepasswd password /path/to/passfile @#
#@ or x11vnc -storepasswd /path/to/passfile @#
#@ or x11vnc -storepasswd @#
#@ @#
#@ (the last one will use ~/.vnc/passwd) @#
#@ @#
#@ and then starting x11vnc via: @#
#@ @#
#@ x11vnc -rfbauth /path/to/passfile @#
#@ @#
#@ an existing ~/.vnc/passwd file from another VNC @#
#@ application will work fine too. @#
#@ @#
#@ You can also use the -passwdfile or -passwd options. @#
#@ (note -passwd is unsafe if local users are not trusted) @#
#@ @#
#@ Make sure any -rfbauth and -passwdfile password files @#
#@ cannot be read by untrusted users. @#
#@ @#
#@ Use x11vnc -usepw to automatically use your @#
#@ ~/.vnc/passwd or ~/.vnc/passwdfile password files. @#
#@ (and prompt you to create ~/.vnc/passwd if neither @#
#@ file exists.) Under -usepw, x11vnc will exit if it @#
#@ cannot find a password to use. @#
#@ @#
#@ @#
#@ Even with a password, the subsequent VNC traffic is @#
#@ sent in the clear. Consider tunnelling via ssh(1): @#
#@ @#
#@ http://www.karlrunge.com/x11vnc/#tunnelling @#
#@ @#
#@ Or using the x11vnc SSL options: -ssl and -stunnel @#
#@ @#
#@ Please Read the documentation for more info about @#
#@ passwords, security, and encryption. @#
#@ @#
#@ http://www.karlrunge.com/x11vnc/faq.html#faq-passwd @#
#@ @#
#@ To disable this warning use the -nopw option, or put @#
#@ 'nopw' on a line in your ~/.x11vncrc file. @#
#@ @#
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
###############################################################
02/08/2024 05:52:18 x11vnc version: 0.9.16 lastmod: 2019-01-05 pid: 9
02/08/2024 05:52:18 XOpenDisplay(":99") failed.
02/08/2024 05:52:18 Trying again with XAUTHLOCALHOSTNAME=localhost ...
02/08/2024 05:52:18 ***************************************
02/08/2024 05:52:18 *** XOpenDisplay failed (:99)
*** x11vnc was unable to open the X DISPLAY: ":99", it cannot continue.
*** There may be "Xlib:" error messages above with details about the failure.
Some tips and guidelines:
** An X server (the one you wish to view) must be running before x11vnc is
started: x11vnc does not start the X server. (however, see the -create
option if that is what you really want).
** You must use -display <disp>, -OR- set and export your $DISPLAY
environment variable to refer to the display of the desired X server.
- Usually the display is simply ":0" (in fact x11vnc uses this if you forget
to specify it), but in some multi-user situations it could be ":1", ":2",
or even ":137". Ask your administrator or a guru if you are having
difficulty determining what your X DISPLAY is.
** Next, you need to have sufficient permissions (Xauthority)
to connect to the X DISPLAY. Here are some Tips:
- Often, you just need to run x11vnc as the user logged into the X session.
So make sure to be that user when you type x11vnc.
- Being root is usually not enough because the incorrect MIT-MAGIC-COOKIE
file may be accessed. The cookie file contains the secret key that
allows x11vnc to connect to the desired X DISPLAY.
- You can explicitly indicate which MIT-MAGIC-COOKIE file should be used
by the -auth option, e.g.:
x11vnc -auth /home/someuser/.Xauthority -display :0
x11vnc -auth /tmp/.gdmzndVlR -display :0
you must have read permission for the auth file.
See also '-auth guess' and '-findauth' discussed below.
** If NO ONE is logged into an X session yet, but there is a greeter login
program like "gdm", "kdm", "xdm", or "dtlogin" running, you will need
to find and use the raw display manager MIT-MAGIC-COOKIE file.
Some examples for various display managers:
gdm: -auth /var/gdm/:0.Xauth
-auth /var/lib/gdm/:0.Xauth
kdm: -auth /var/lib/kdm/A:0-crWk72
-auth /var/run/xauth/A:0-crWk72
xdm: -auth /var/lib/xdm/authdir/authfiles/A:0-XQvaJk
dtlogin: -auth /var/dt/A:0-UgaaXa
Sometimes the command "ps wwwwaux | grep auth" can reveal the file location.
Starting with x11vnc 0.9.9 you can have it try to guess by using:
-auth guess
(see also the x11vnc -findauth option.)
Only root will have read permission for the file, and so x11vnc must be run
as root (or copy it). The random characters in the filenames will of course
change and the directory the cookie file resides in is system dependent.
See also: http://www.karlrunge.com/x11vnc/faq.html