I'm seeing these pop-ups frequenty now. Seems like, every time I update CDVR?
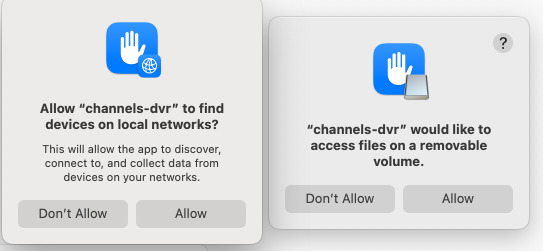
Of course it's not a big deal to click "Allow" but this also means updates applied remotely via the web admin page, will halt the Channels server from working, until those permissions are re-granted once again.
Is anyone else experiencing this? Is there a way to "whitelist" channels-dvr permanently so I don't have to keep granting it permission to "find devices on local networks" and "access files on my removable volumes" every time I update? Feels like this is new behavior with macOS Sequoia. At least, I've updated CDVR remotely via the web admin for years now, and have never experienced this issue before.
Consider this a heads up, if you're also running CDVR server on macOS Sequoia. I think this might be an issue for more folks moving forward.